Network Monitoring in new 5G Cloud Networks
Introduction
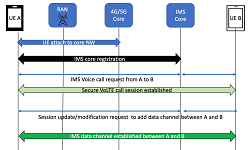
In any mobile network, network monitoring is a crucial and enabler for network management. Its importance is growing with the adoption of virtualization and continuous increase in network traffic.
A monitoring system collects the network statistics, traffic flows, and application and user profiles at various intervals and granularities to evaluate the status of the network for management tasks such as anomaly detection, network forensics, load balancing, traffic engineering, and enforcing Service Level Agreements (SLA), QoS/QoE and network maintenance. Therefore, a network monitoring system should be capable of monitoring the network and traffic flows at different granularities and for obtaining measureable metrics such as level of aggregation, time intervals, bandwidth utilization and accuracy.
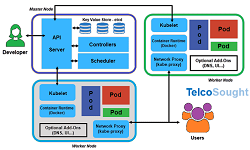
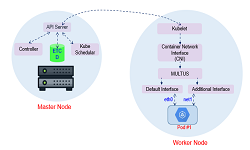
Network transformations in 5G is making use of two new concepts: Network Functions Virtualization (NFV) and the Software Defined Networks (SDN). SDN decouples the network control and data planes and enable programmability by introducing programmable interface into their networking equipment. As SDN, networks allow centralized controllers and the network components have programmable interfaces, network monitoring is augmented to a higher level in terms of efficiency, cost and complexity. NFV is ETSI standardized architecture and enables network functions to run as a service in commercial off‐the‐shelf hardware. NFV and SDN based architecture-introduced novel monitoring to overcome the limitations of legacy monitoring system.
Traditional Network Monitoring Techniques

- SNMP [Simple Network Monitoring Protocol]: SNMP is old age protocol used for networking monitoring using the MIBs. It does allow to manage Network Elements (NEs) and high‐level information on resource use e.g. monitor bandwidth usage of routers and switches port‐by‐port, device information like memory use, CPU load, etc.;
- RMON [Remote Monitoring]: Remote network monitoring (RMON) is the process of monitoring network traffic on a remote Ethernet segment to detect network issues such as dropped packets, network collisions and traffic congestion. RMON was developed by IETF. An RMON typically operates in a client/server model. Monitoring devices commonly called “probes” contain RMON software agents that collect information and analyse packets. These probes act as servers and the Network Management applications that communicate with them act as clients. While both agent configuration and data collection use SNMP, RMON is designed to operate differently than other SNMP-based systems.
- Netflow or sFlow: While collecting information on IP, network flows and bandwidth usage. These protocols are mostly dedicated for performance analysis and network management and does packet sniffing such as Deep Packet Inspection, Deep Flow Inspection, virus scanners, malware detectors and other techniques for analysing network packet headers, complete packets or packet payloads.
Monitoring Techniques in 5G Networks
- Active Probing: Active Probes acts with service‐centric approach to collects data based on synthetic measurements, i.e. ICMP Echo Requests, HTTP GET requests or specially crafted packets. Often these measurements are trying to analyse properties of the network that would be impossible to capture from pure passive measurements and are arguably the only way to measure service availability.
- Device Polling: Device Polling is a device‐centric approach that queries devices typically using SNMP (Simple Network Management Protocol), collecting interface status information, traffic volumes, device load, CPU usages, etc.;
- Flow Collection: Flow Collections solutions collect traffic information from network devices such as routers/switches. Here traffic can be aggregated in flows using, e.g. Cisco Netflow and stored on disk for post‐analysis. Flow data is easier to analyse and process than packet data, but provides less granular information;
- Packet Analysis: This usually involves a SPAN port from a switch or a network tap and extracts information from individual packets, including information from payloads through DPI (Deep Packet Inspection);
- Log Analysis: Log Analysis solutions collect machine-generated data typically in the form of log files (e.g. syslog, varlog) and present a query interface to correlate events across different types of systems, e.g. routers, web servers, load balancers.
Related Posts: